For more than seven years, organizations around the world have trusted Bugcrowd to help identify more than 300,000 vulnerabilities in their known IT ecosystems. But with the average organization tracking less than 40% of their total internet-facing footprint, and more than one-third of successful cyber attacks occurring via unknown or un-prioritized assets, it’s clear that the first step in defending your attack surface is knowing where it is.
To help organizations close this gap and restore their Defender’s Advantage, Bugcrowd launched Attack Surface Management (ASM). As the latest risk-based solution to join the Bugcrowd security stack, ASM enables organizations to look beyond their known digital footprint for the lost, forgotten, or un-prioritized assets that attackers target first. When priority assets are identified, organizations have the option to roll these assets under coverage through any of Bugcrowd’s active crowdsourced security testing programs.
Crowd-Powered Discovery
In October, we told you about Asset Risk, Attack Surface Management’s crowd-powered flagship solution for reducing unknown attack surface. Asset Risk combines human ingenuity with insights gleaned from over 1,200 managed programs to help customers find, connect, and prioritize more of their unknown attack surface before it can be compromised. But what about those that require more control over what’s uncovered?
Continuous Control
One month on from the successful launch of Asset Risk, Bugcrowd is thrilled to announce the latest addition to the Attack Surface Management suite, Asset Inventory. Asset Inventory is a software-based complement to Asset Risk which provides continual discovery, inventory, alerting, and management controls for every organization’s internet-facing asset map. Fed by years of internet data, and powered by the flexible querying and rules-based alerting system we know customers need, Asset Inventory provides the visibility and control required to effectively manage the world’s most dynamic attack surfaces.
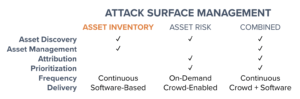
Figure 1: The two solutions can be operated independently, in combination, or in connection with any of our other platform security solutions.
How it Works
Setting up Asset Inventory is quick and easy, with results populating in a matter of seconds.
- Add: Add domain names to your inventory; subdomains get instantly added.
- Fingerprint: Extensive technology fingerprinting is applied to each asset in your inventory.
- Suggest: Other domain names that you own are suggested to you as possible additions.
- Automate: Continuous discovery keeps your inventory up to date, and alerts you of changes.
Key Use Cases
Asset Inventory fulfills a variety of business use cases including those particular to security, IT, compliance, and even marketing:
- Determine use of publicly accessible technology like server-software, javascript library, or open ports
- Manage certificates and receive alerts before expiration
- Compile a complete list of all domain names and subdomains that your organization owns
- See and quickly act on changes to your technology, domains, and subdomains.
Key Features
Beyond domains and subdomains, Asset Inventory catalogs all IT it encounters via technology fingerprinting to provide more insight and context around every uncovered asset. Because many organizations fail to track changes to infrastructure — servers brought online, ports opened, software changes, etc. — Asset Inventory also enables “smart folder” creation and alerting to quickly categorize and flag high-risk asset-related events which can then be quickly exported and shipped to the appropriate team via Slack, ServiceNow, or email integrations. Additionally, Asset Inventory offers:
- Near-real time inventory population of domains and subdomains
- Continuous discovery using 18 methodologies for asset identification and attribution
- Web-based portal with publicly accessible services for cross-organization collaboration
- Easy API integration to fit into your existing security ecosystem
- Live alerting for aberrant discoveries like open ports, expired SSL/TLS Certs, or new technology
- In-depth querying for hundreds of asset attributes like SSH server version.
Bugcrowd’s Asset Inventory is the latest step forward in helping organizations take back control of their digital ecosystems. To read more about Asset Inventory or the Attack Surface Management suite, check out our solution page.